System integrity – protect your automation systems
The basic rule for industrial companies is to ensure uninterrupted production. Thus, it is important to protect automation systems from tampering and unauthorized access.
Siemens’ security functions offer comprehensive protection against unauthorized network access as well as configuration changes at the control level.
System integrity access control
Increasing Demand for Security (audit trail): Unintentional operating errors or deliberate manipulations jeopardize the plant security and must therefore be avoided. Additionally, there are specific requirements for traceability, which include documenting operations and changes.
This includes recording what changes were made, when, and by whom. Furthermore, regulations and requirements, such as those of the FDA, must be complied with.
Challenges:
Unauthorized access to machines and systems must be prevented during operation and maintenance phases to avoid delays or damage in production. Protecting trade secrets, such as recipes, is also of great importance. Other challenges include the requirements for traceability and documentation, as well as the individual management of access rights.
Solution
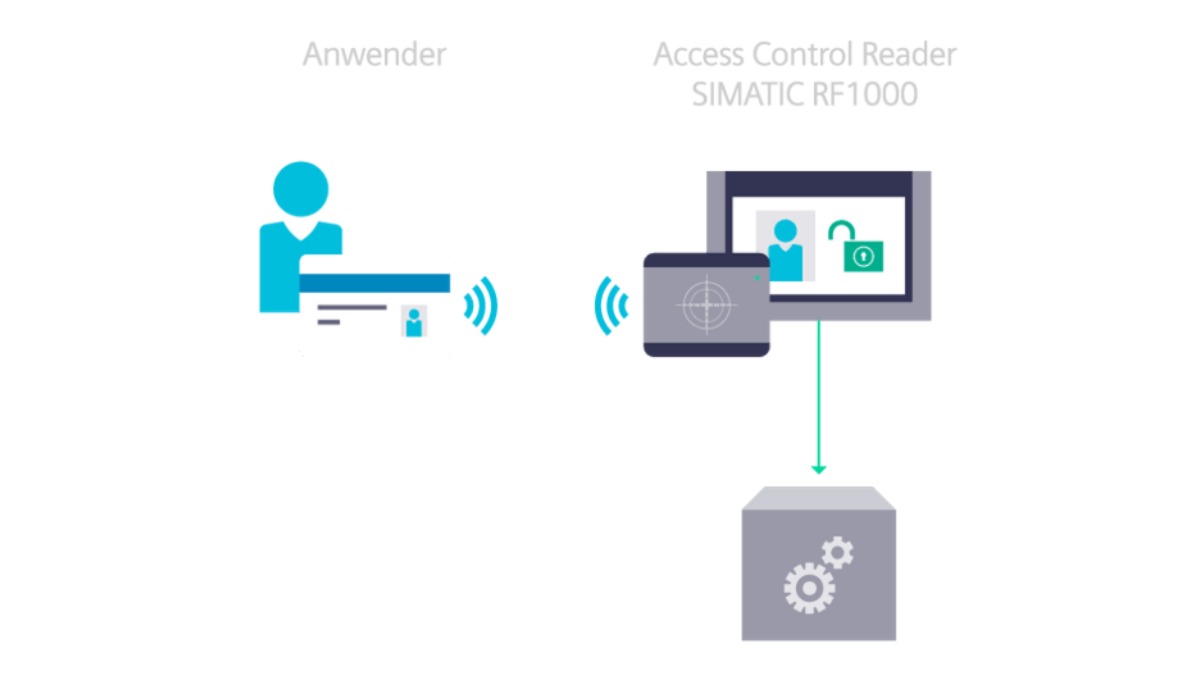
The unique identification of operating personnel on machines and plants includes both access control and the audit trail. The Access Control Reader SIMATIC RF1000 from Siemens supports both one-time and permanent reading with the RFID card, as well as reading with the RFID card in combination with user login credentials.
This includes:
- One-time reading of the ID card
- Permanent reading of the ID card
- One-time reading of the ID card with additional user-specific password authentication
Technical solution
The connectivity concept of the SIMATIC RF1000 includes connection via USB 2.0 to Windows-based PCs or HMI systems and is compatible with PM LOGON for local and central user management. Additionally, it offers a serial connection via RS232 (ET 200SP, SIMATIC RF100C, PCs, third-party HMI systems).
The connectivity concept of the SIMATIC RF1100 enables connection via Ethernet (ModbusTCP or XML) to PCs, PLCs, SIMATIC LOGO!, or HMI systems and is also compatible with PM LOGON for local and central user management. It also integrates Power over Ethernet (PoE).
Benefit
Secured machine access
- Reliable limitation of malfunctions
- Prevention of unauthorized operation
- Avoidance of operational errors and downtimes through secure and documented access to machines
Customized access rights
- Assignment of different access rights
- Use of existing employee ID cards for a cost-effective solution
- Manage and store user-specific instructions
Process reliability
- Designed for seamless integration into the company-wide Industrial Cybersecurity concept
- Logging of all access data
- Traceability of access and parameter changes
- Compliance with documentation standards