Cybersecurity for Industry
Connect the real and digital world and become a Digital Enterprise with Siemens.
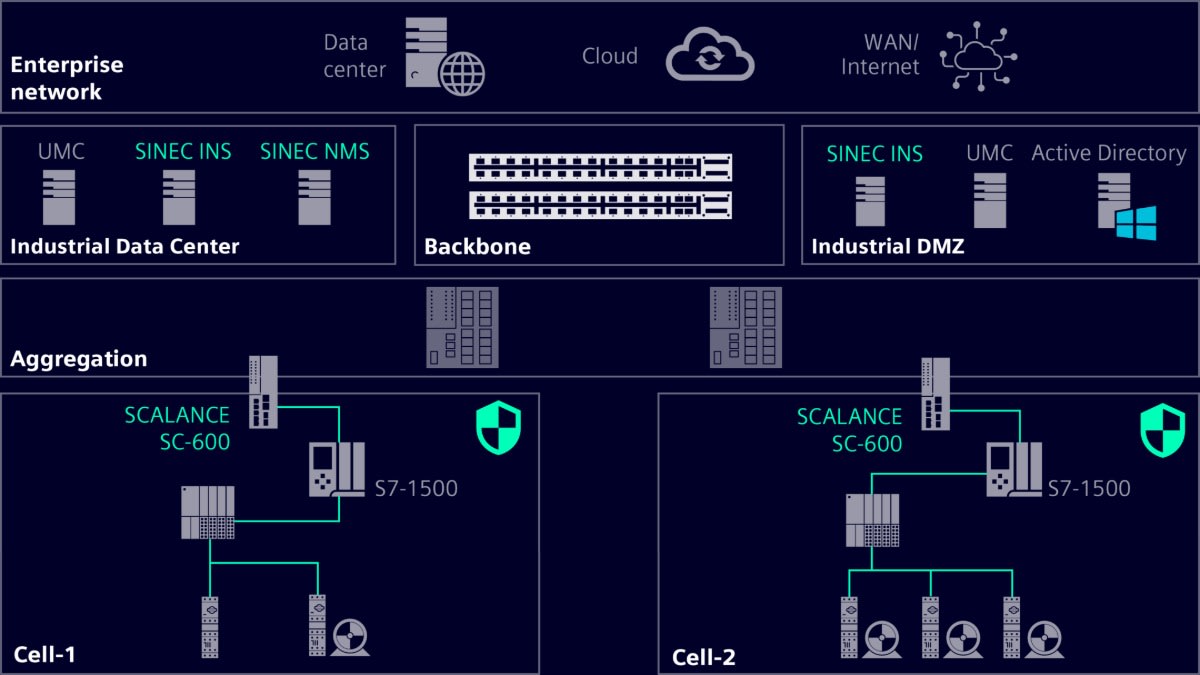
Industrial Cybersecurity protects your IT/OT integration with its comprehensive cybersecurity concept, Defense in Depth.
Protected in every aspect - Defense in Depth
Industrial Security components from Siemens are specifically optimized for use in automation technology and meet the special requirements of Industrial Communication networks.
To protect industrial networks and ensure secure remote access, Siemens offers a wide range of products with integrated security functions (Security Integrated). These include the Industrial Security Appliances SCALANCE S, the Industrial Routers SCALANCE M for wired and mobile wireless networks (4G/5G), and the security communication processors for SIMATIC S7 controllers.
These products support a stateful inspection firewall and also secure VPN communication (Virtual Private Network) to protect against unauthorized access, data espionage, and manipulation.
All devices can be configured in the TIA Portal, enabling consistent end-to-end security engineering. With the SINEC software solutions, it is also possible to monitor, manage, and configure complex industrial networks, including firewall rules (SCALANCE S), centrally and around the clock, including in security-related areas.
Highlights
Offering based on extensive experience from Siemens' own plants.
Broad portfolio with integrated security features.
Proactive approach with vulnerability processes and security consultations enables Siemens to keep products secure.
Comprehensive services for plant and network security as well as system integrity.